Weekend Project: Hacking the Square Reader
Originally published on my old blog in 2013.
Introduction
I’ve been interested in looking at the information contained in credit cards ever since I first heard about the Square card reader. The idea of such a tiny device being able to parse all the information on a credit card directly into your phone is fascinating to me and I wanted to figure out how it worked and if I could play with it a little bit. Unfortunately, Square moved from a very simple circuit design to a larger, encrypted version before I got mine. Coming into this weekend, I didn’t even have the expertise to figure out the simple version, much less the encrypted version and so I had mostly given up on working with credit card information.
However, one of my friends happened to have a few of the old Square readers that he gave me to work with. That gave me the opportunity to see what I could do and start hacking on this project.
Software
My first goal was just to read data off a credit card (or any other card with a magstripe) with the Square reader. Jeffrey Malone has put together a couple excellent libraries for parsing data off the unencrypted Square reader, so I jumped right into those. I downloaded MagRead and built it, as below (from the command line):
git clone https://github.com/ieatlint/MagRead.git
cd MagRead
qmake MagRead.pro
make
open -a MagRead.appThen I plugged the Square reader into my computer, started scanning, and slid my card through. Note that this only works with audio jacks that are both the microphone and speaker jack, like on MacBooks or ThinkPads. The app worked exactly as advertised and instantly displayed my credit card number and expiration date. I tried scanning some other cards (my student ID, insurance card, AAA card, etc.) and they all worked, displaying some of the information they contained.
After reading a bit more about how credit card magstripe encoding works, I learned that there are typically three tracks on the magstripe. Track 3 includes a variety of miscellaneous information, track 2 is the normal track with the card number and expiration date (along with a couple other pieces of information), and track 1 has everything on track 2 plus the cardholder’s name and the CVV (different from what most people consider the CVV on the back of the card). If you’re interested in learning more, I highly recommend checking out this website on credit card information.
I learned that the Square reader reads track 2 by default, but by putting a shim into the reader that’s about .11 inches thick, you could get it to read track 1 instead. I found that a zip tie did the trick and I could start reading the first track, which revealed some more information. MagRead continued to display this input perfectly, but it didn’t display the discretionary data on the track, which includes the CVV.


It turns out that the author of MagRead released another library called SWipe that dumps all the information read. I went through much the same process to get it to work, cloning it from GitHub, qmake’ing it, make’ing it, and then opening the resulting application. Now when I scanned the cards I could see everything on them, in the following format:
$B################^BROMBERG/ANDREW A^1408101##############?
Here’s a breakdown of what’s there:
$ : Start of sequence
B : Indicates a bank-issued card
#s : Card number
^ : Separator
BROMBERG/ANDREW A : My name
^ : Separator
1408 : The expiration date (August 2014)
101 : The card service code, indicating that the card can be used
internationally and without restrictions
#s : The discretionary data, including the CVV
? : The end-of-sequence marker
Similarly, I could see more information from other cards by scanning their first track as opposed to the second track.
Hardware
This was very cool, but I wasn’t satisfied yet. I wanted to know more about how and why the Square reader actually works. Thankfully I live in the same house as Jonathan Friedman, who runs CircuitHubIf you’re interested in electronics and don’t know CircuitHub yet, you should. They’re building a free, universal parts library that makes it incredibly easy to pick out the parts you need. and has a PhD in Electrical Engineering. He spent a couple hours teaching me about electricity and magnetism from the ground up (which I’ll spare you in this blog post) and explained the principles behind magnetic card readers. If you’re interested in learning more about how they work, please email me and I’d be happy to talk to you, but there’s a large enough amount of background knowledge required that I don’t think it’s appropriate for this blog post.
Jonathan suggested that we try to dive into the electronics of the reader to help me better visualize what’s going on — so we did exactly that.

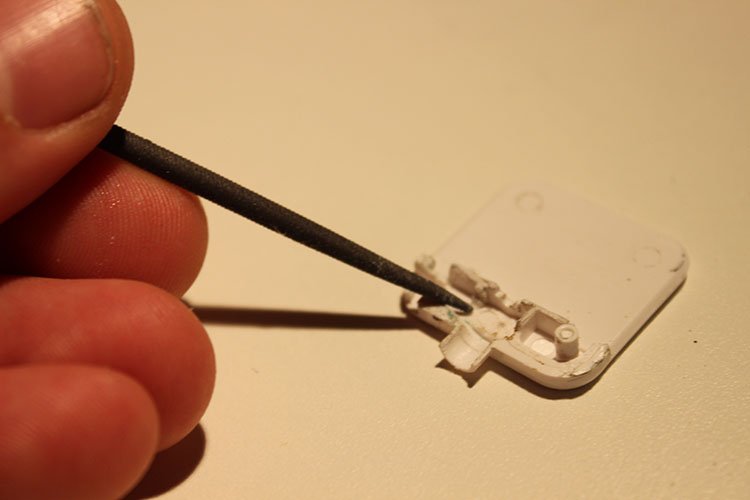
Our first step was to open the reader up so we could see the innards, which were actually really simple. The most prominent component is a magnetic head that is capable of detecting magnetic changes that are very close to it. This is then attached to two wires that are soldered onto the connector.
The wires in the reader connect to the ground and microphone segments of the connector. This means that the connector propagates a voltage differential (generated in the magnetic read head) into the computer or phone, which can then be parsed into the desired information. We decided to tap the internal part of the connector (where the original wires are connected) with our own wires to facilitate attachment to an oscilloscope to measure the output and visualize the results.

Jonathan soldered a couple wires on very delicately while I whittled the top half of the Square reader so that we could place it back on top without the new wires interfering with the placement.

Finally we plugged our wires into the oscilloscope and started swiping a card through the reader.
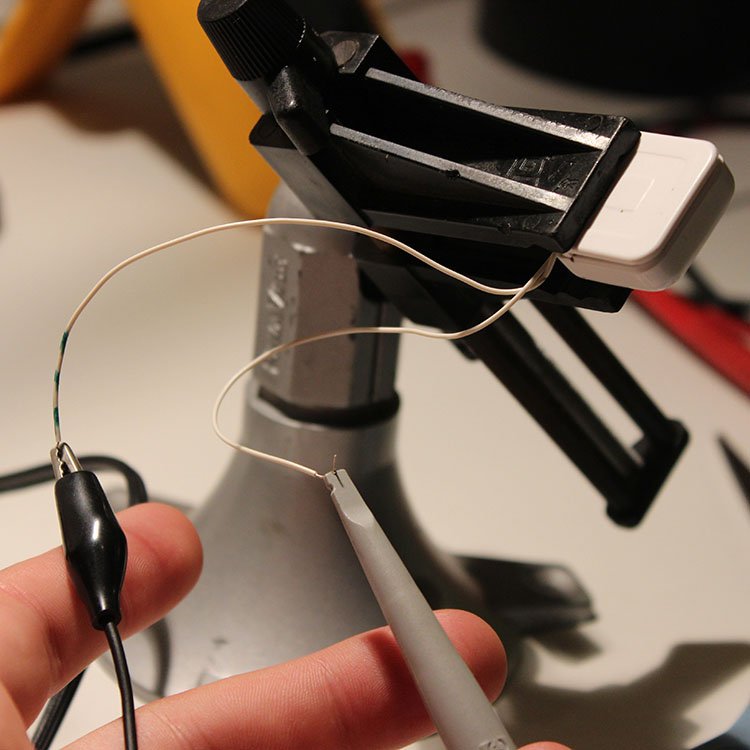

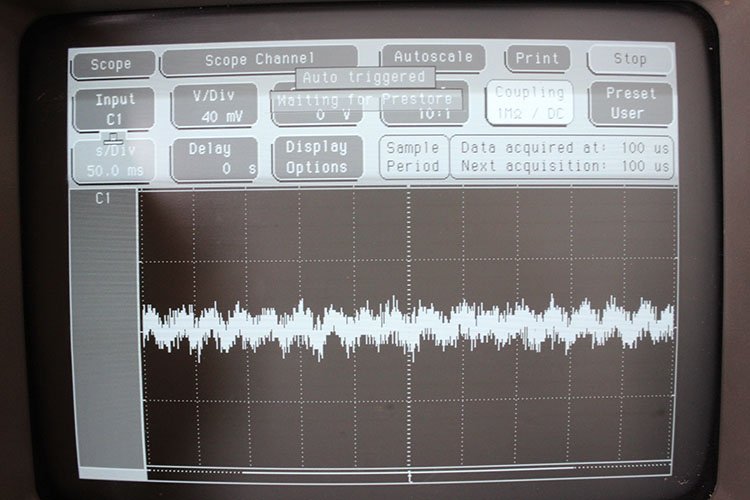
Unfortunately, no matter how much tuning we did, we couldn’t see anything. The Square reader doesn’t actually have an amplifier in it, just a raw magnetic transducer so the signal is very weak. We measured the reader’s impedance at 5.375k Ohms. With the oscilloscope set to its 1 million ohm input impedance setting, the wiring detected the 60Hz airborne signal emanating from the power grid strongly enough to make decoding of the card reader’s signal extremely difficult.
The oscilloscope at the 1 million ohm impedance setting. Only the 60Hz power grid signal is visible.
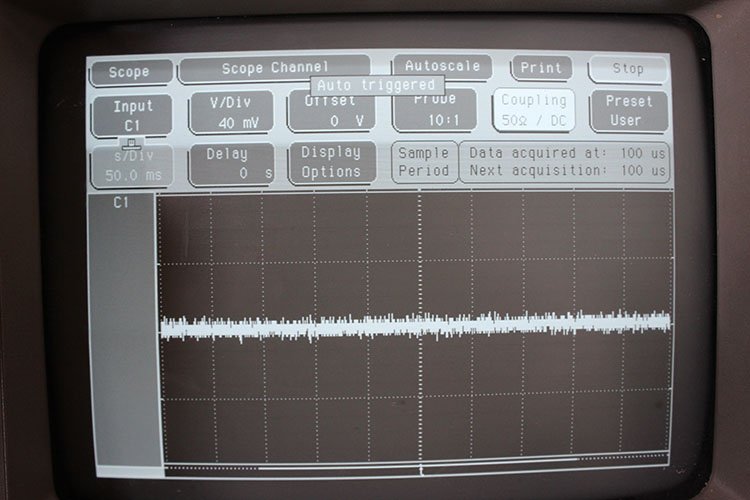
Switching to the oscilloscope’s low (50 ohm) impedance setting largely eliminated the influence of the airborne signal, but reduced the reader’s signal by more than 100x — to the point where we could no longer see it.
The oscilloscope at the 50 ohm impedance setting. No signal is visible at all.
Jonathan explained to me that Ohm’s law (voltage being generally current times impedance) implies that a large input impedance allows very weak induced currents to turn into comparatively large voltages. This is why the airborne power grid current turned into a very large displayed voltage in the oscilloscope at the 1 million ohm impedance setting.
Jonathan suggested that we try an intermediate impedance value between 50 ohms and 1 million ohm, which we managed by putting a resistor in parallel with the circuit while setting the oscilloscope to the 50 ohm setting. We went with about 360k ohms. This was perfect, and we could suddenly see my credit card data being displayed as waveforms on the screen as I swiped it! Here’s a picture of one of the digits of my credit card number:

What’s so amazing about this for me is that I could see the waveform representing the data on my card — the very same data that MagRead and SWipe and the Square app take in to parse and output as numbers. With some signal processing, we could actually refine the data on the oscilloscope and get the credit card information right out of it!
Conclusion
There are a few ways I’d like to go with this project now that I have a solid baseline.
- I want to read track 3 on credit cards and try to parse through that information to figure out what’s actually there. That will involve rigging the reader in such a way that I can offset the card correctly while reading the information.
- I want to try to do some signal processing on the oscilloscope output to actually parse some data out myself, without the help of MagRead or SWipe.
- Now that I know a tiny bit about electricity and magnetism, I want to learn more, especially about practical circuitry design and modification. I would really like to be able to hack electronics effectively as well as understand what’s going on in the things I use every day.
If you have any questions or comments on this post, please don’t hesitate to email me! I’d love to answer any questions you might have and if there’s any suggestions you have, please let me know.
Looking for more to read?
Want to hear about new essays? Subscribe to my roughly-monthly newsletter recapping my recent writing and things I'm enjoying:
And I'd love to hear from you directly: andy@andybromberg.com